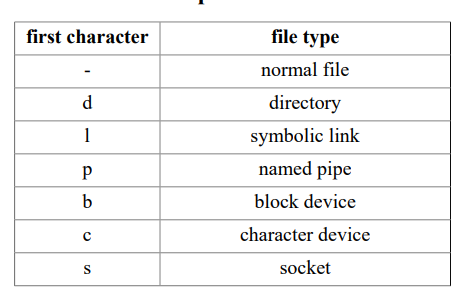
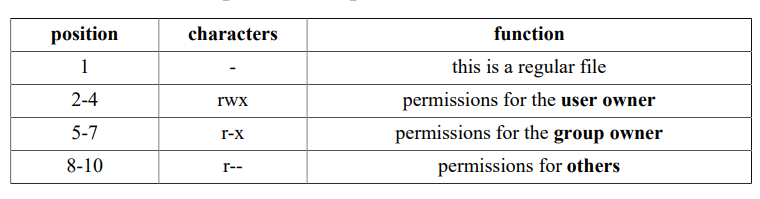
A Linux distribution is a collection of (usually open source) software on top of a Linux kernel. A distribution (or short, distro) can bundle server software, system management tools, documentation and many desktop applications in a central secure software repository.
A distro aims to provide a common look and feel, secure and easy software management and often a specific operational purpose.
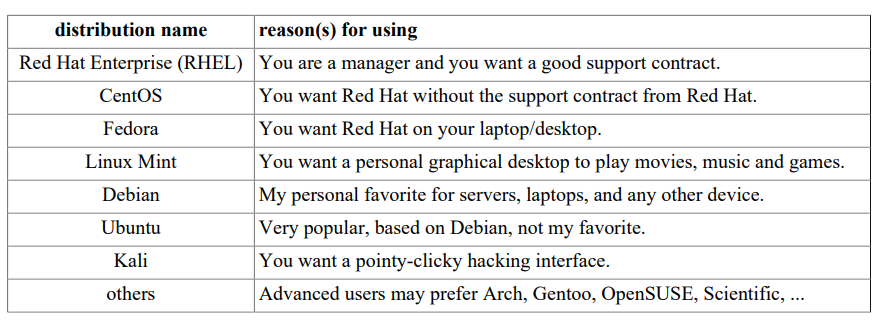
Let’s take a look at some popular distributions
Red Hat:
Red Hat is a billion dollar commercial Linux company that puts a lot of effort in developing Linux. They have hundreds of Linux specialists and are known for their excellent support. They give their products (Red Hat Enterprise Linux and Fedora) away for free. While Red Hat Enterprise Linux (RHEL) is well tested before release and supported for up to seven years after release, Fedora is a distro with faster updates but without support.
Ubuntu:
Canonical started sending out free compact discs with Ubuntu Linux in 2004 and quickly became popular for home users (many switching from Microsoft Windows). Canonical wants Ubuntu to be an easy to use graphical Linux desktop without need to ever see a command line. Of course they also want to make a profit by selling support for Ubuntu
Debian:
There is no company behind Debian. Instead there are thousands of well organised developers that elect a Debian Project Leader every two years. Debian is seen as one of the most stable Linux distributions. It is also the basis of every release of Ubuntu. Debian comes in three versions: stable, testing and unstable. Every Debian release is named after a character in the movie Toy Story.
Other:
Distributions like CentOS, Oracle Enterprise Linux and Scientific Linux are based on Red Hat Enterprise Linux and share many of the same principles, directories and system administration techniques. Linux Mint, Edubuntu and many other *buntu named
distributions are based on Ubuntu and thus share a lot with Debian. There are hundreds of other Linux distributions
Which to choose ?
Working with directories
1. Display your current directory. pwd 2. Change to the /etc directory. cd /etc 3. Now change to your home directory using only three key presses. cd (and the enter key) 4. Change to the /boot/grub directory using only eleven key presses. cd /boot/grub (use the tab key) 5. Go to the parent directory of the current directory. cd .. (with space between cd and ..) 6. Go to the root directory. cd / 7. List the contents of the root directory. ls 8. List a long listing of the root directory. ls -l 9. Stay where you are, and list the contents of /etc. ls /etc 10. Stay where you are, and list the contents of /bin and /sbin. ls /bin /sbin 11. Stay where you are, and list the contents of ~. ls ~ 12. List all the files (including hidden files) in your home directory. ls -al ~ 13. List the files in /boot in a human readable format. ls -lh /boot 14. Create a directory testdir in your home directory. mkdir ~/testdir
Linux file tree
root directory /
All Linux systems have a directory structure that starts at the root directory. The root directory is represented by a forward slash, like this: /.
Everything that exists on your Linux system can be found below this root directory. Let's take a brief look at the contents of the root directory
[oracle@localhost ~]$ ls /
bin boot dev etc home lib lib64 media mnt opt proc root run sbin srv sys tmp u01 usr var
Binary directories
Binaries are files that contain compiled source code (or machine code). Binaries can be executed on the computer. Sometimes binaries are called executables.
/bin
The /bin directory contains binaries for use by all users. According to the FHS the /bin directory should contain /bin/cat and /bin/date (among others).
[oracle@localhost ~]$ ls /bin
[ hivexsh printf
a2p host prlimit
ab hostid processcsv.py
abrt-action-analyze-backtrace hostname procmail
abrt-action-analyze-c hostnamectl profiles
abrt-action-analyze-ccpp-local hpcups-update-ppds prove
abrt-action-analyze-core hpijs prtstat
abrt-action-analyze-oops hsqldbRunUtil prune
abrt-action-analyze-python htdbm ps
abrt-action-analyze-vmcore htdigest ps2ascii
abrt-action-analyze-vulnerability htpasswd ps2epsi
abrt-action-analyze-xorg HttpClient ps2pdf
abrt-action-check-oops-for-hw-error httxt2dbm ps2pdf12
abrt-action-generate-backtrace hugeadm ps2pdf13
abrt-action-generate-core-backtrace hugectl ps2pdf14
abrt-action-install-debuginfo hugeedit ps2pdfwr
abrt-action-list-dsos huge_page_setup_helper.py ps2ps
abrt-action-notify hunspell ps2ps2
abrt-action-perform-ccpp-analysis hwloc-annotate psed
abrt-action-save-kernel-data hwloc-assembler psfaddtable
/sbin /sbin contains binaries to configure the operating system. Many of the system binaries require root privilege to perform certain tasks.
/lib Binaries found in /bin and /sbin often use shared libraries located in /lib. Below is a screenshot of the partial contents of /lib.
[oracle@localhost ~]$ ls /lib
alsa dracut hsqldb jvm libopamgt.so mozilla python3.6 tmpfiles.d
binfmt.d firewalld java jvm-commmon libopamgt.so.0 NetworkManager rpm tuned
bonobo firmware java-1.5.0 jvm-exports libopamgt.so.0.4.0 opa sendmail udev
cpp fontconfig java-1.6.0 jvm-private locale openslp-server sendmail.postfix x86_64-redhat-linux6E
crda games java-1.7.0 kbd modprobe.d oracleasm sse2 yum-plugins
cups gcc java-1.8.0 kdump modules polkit-1 sysctl.d
debug grub java-ext kernel modules-load.d python2.7 systemd
/opt The purpose of /opt is to store optional software. In many cases this is software from outside the distribution repository. You may find an empty /opt directory on many systems. A large package can install all its files in /bin, /lib, /etc subdirectories within /opt/ $packagename/. If for example the package is called wp, then it installs in /opt/wp, putting binaries in /opt/wp/bin and manpages in /opt/wp/man
Configuration directories
/boot The /boot directory contains all files needed to boot the computer. These files don't change very often. On Linux systems you typically find the /boot/grub directory here. /boot/grub contains /boot/grub/grub.cfg (older systems may still have /boot/grub/grub.conf) which defines the boot menu that is displayed before the kernel starts.
/etc All of the machine-specific configuration files should be located in /etc. Historically /etc stood for etcetera, today people often use the Editable Text Configuration backronym. Many times the name of a configuration files is the same as the application, daemon, or protocol with .conf added as the extension
[oracle@localhost ~]$ ls /etc/*.conf
/etc/asound.conf /etc/extlinux.conf /etc/libaudit.conf /etc/numad.conf /etc/softhsm2.conf
/etc/autofs.conf /etc/fprintd.conf /etc/libuser.conf /etc/oddjobd.conf /etc/sos.conf
/etc/autofs_ldap_auth.conf /etc/fuse.conf /etc/locale.conf /etc/pbm2ppa.conf /etc/srp_daemon.conf
/etc/brltty.conf /etc/GeoIP.conf /etc/logrotate.conf /etc/pcp.conf /etc/sudo.conf
/etc/cgconfig.conf /etc/host.conf /etc/man_db.conf /etc/pnm2ppa.conf /etc/sudo-ldap.conf
/etc/cgrules.conf /etc/idmapd.conf /etc/mke2fs.conf /etc/radvd.conf /etc/sysctl.conf
/etc/cgsnapshot_blacklist.conf /etc/ipsec.conf /etc/mtools.conf /etc/request-key.conf /etc/tcsd.conf
/etc/chrony.conf /etc/iwpmd.conf /etc/named.conf /etc/resolv.conf /etc/updatedb.conf
/etc/dleyna-server-service.conf /etc/kdump.conf /etc/nfs.conf /etc/rsyncd.conf /etc/usb_modeswitch.conf
/etc/dnsmasq.conf /etc/krb5.conf /etc/nfsmount.conf /etc/rsyslog.conf /etc/vconsole.conf
/etc/dracut.conf /etc/ksmtuned.conf /etc/nsswitch.conf /etc/sestatus.conf /etc/wvdial.conf
/etc/e2fsck.conf /etc/ld.so.conf /etc/ntp.conf /etc/slp.conf /etc/yum.conf
/etc/init.d/ A lot of Unix/Linux distributions have an /etc/init.d directory that contains scripts to start and stop daemons. This directory could disappear as Linux migrates to systems that replace the old init way of starting all daemons. /etc/X11/ The graphical display (aka X Window System or just X) is driven by software from the X.org foundation. The configuration file for your graphical display is /etc/X11/xorg.conf. /etc/skel/ The skeleton directory /etc/skel is copied to the home directory of a newly created user. It usually contains hidden files like a .bashrc script. /etc/sysconfig/ This directory, which is not mentioned in the FHS, contains a lot of Red Hat Enterprise Linux configuration files.
In memory directories
/dev
Device files in /dev appear to be ordinary files, but are not actually located on the hard disk.
The /dev directory is populated with files as the kernel is recognising hardware.
common physical devices
Common hardware such as hard disk devices are represented by device files in /dev. Below a screenshot of SATA device files on a laptop and then IDE attached drives on a desktop.
(The detailed meaning of these devices will be discussed later.)
[oracle@localhost ~]$ ls /dev/sd*
/dev/sda /dev/sda1 /dev/sda2 /dev/sdb /dev/sdb1 /dev/sdb2 /dev/sdb3
/var variable data
Files that are unpredictable in size, such as log, cache and spool files, should be located in /var.
/var/log The /var/log directory serves as a central point to contain all log files.
[oracle@localhost ~]$ ls /var/log
amanda dirsrv messages-20230423 spooler Xorg.1.log.old
anaconda dmesg ntpstats spooler-20230406 Xorg.2.log
audit dmesg.old openlmi-install.log spooler-20230413 Xorg.2.log.old
boot.log firewalld oracleasm spooler-20230416 Xorg.3.log
boot.log-20221203 gdm oracle-database-preinstall-19c spooler-20230423 Xorg.3.log.old
boot.log-20221210 glusterfs oracle-database-server-12cR2-preinstall sssd Xorg.4.log
boot.log-20230406 grubby oracleohasd swtpm Xorg.4.log.old
boot.log-20230416 grubby_prune_debug pcp tallylog Xorg.5.log
boot.log-20230417 httpd pki tomcat Xorg.5.log.old
boot.log-20230420 lastlog pluto tuned Xorg.6.log
boot.log-20230426 libvirt ppp vboxadd-install.log Xorg.6.log.old
btmp maillog qemu-ga vboxadd-setup.log Xorg.7.log
btmp-20230406 maillog-20230406 sa vboxadd-setup.log.1 Xorg.7.log.old
chrony maillog-20230413 samba vmware-vmtoolsd-root.log Xorg.8.log
cron maillog-20230416 sa-update.log vmware-vmusr-root.log Xorg.8.log.old
cron-20230406 maillog-20230423 secure wpa_supplicant.log Xorg.9.log
cron-20230413 mariadb secure-20230406 wtmp Xorg.9.log.old
cron-20230416 messages secure-20230413 Xorg.0.log yum.log
cron-20230423 messages-20230406 secure-20230416 Xorg.0.log.old yum.log-20230406
cups messages-20230413 secure-20230423 Xorg.10.log
custodia messages-20230416 speech-dispatcher Xorg.1.log
/var/log/messages A typical first file to check when troubleshooting on Red Hat (and derivatives) is the /var/ log/messages file. By default this file will contain information on what just happened to the system. The file is called /var/log/syslog on Debian and Ubuntu
[root@localhost ~]# tail /var/log/messages
Apr 26 14:24:36 localhost pulseaudio[3328]: [alsa-sink-Intel ICH] alsa-sink.c: We were woken up with POLLOUT set -- however a subsequent snd_pcm_avail() returned 0 or another value < min_avail.
Apr 26 14:26:14 localhost dbus[841]: [system] Activating via systemd: service name='net.reactivated.Fprint' unit='fprintd.service'
Apr 26 14:26:14 localhost systemd: Starting Fingerprint Authentication Daemon...
Apr 26 14:26:14 localhost kernel: xfs filesystem being remounted at /tmp supports timestamps until 2038 (0x7fffffff)
Apr 26 14:26:14 localhost kernel: xfs filesystem being remounted at /var/tmp supports timestamps until 2038 (0x7fffffff)
Apr 26 14:26:14 localhost dbus[841]: [system] Successfully activated service 'net.reactivated.Fprint'
Apr 26 14:26:14 localhost systemd: Started Fingerprint Authentication Daemon.
Apr 26 14:26:16 localhost su: (to root) oracle on pts/0
Apr 26 14:26:16 localhost dbus[841]: [system] Activating service name='org.freedesktop.problems' (using servicehelper)
Apr 26 14:26:16 localhost dbus[841]: [system] Successfully activated service 'org.freedesktop.problems'
[root@localhost ~]#
whoami The whoami command tells you your username. who The who command will give you information about who is logged on the system. w The w command shows you who is logged on and what they are doing. id The id command will give you your user id, primary group id, and a list of the groups that you belong to.
[root@localhost ~]# whoami
root
[root@localhost ~]#
[root@localhost ~]# who
oracle :0 2023-04-26 14:00 (:0)
oracle pts/0 2023-04-26 14:08 (:0)
[root@localhost ~]# w
14:37:17 up 37 min, 2 users, load average: 0.07, 0.25, 0.45
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
oracle :0 :0 14:00 ?xdm? 2:48 0.37s /usr/libexec/gnome-session-binary --session gnome-classic
oracle pts/0 :0 14:08 1.00s 0.26s 2.24s /usr/libexec/gnome-terminal-server
[root@localhost ~]# id
uid=0(root) gid=0(root) groups=0(root) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
[root@localhost ~]#
sudo su - On some Linux systems like Ubuntu and Xubuntu, the root user does not have a password set. This means that it is not possible to login as root (extra security). To perform tasks as root, the first user is given all sudo rights via the /etc/sudoers. In fact all users that are members of the admin group can use sudo to run all commands as root.
useradd You can add users with the useradd command. The example below shows how to add a user named yanina (last parameter) and at the same time forcing the creation of the home directory (-m), setting the name of the home directory (-d), and setting a description (-c).
[root@localhost ~]# useradd -m -d /home/asr -c "Anish" Anish
[root@localhost ~]# tail -1 /etc/passwd
Anish:x:54332:54332:Anish:/home/asr:/bin/bash
userdel You can delete the user yanina with userdel. The -r option of userdel will also remove the home directory
[root@localhost ~]# userdel -r Anish
[root@localhost ~]# tail -1 /etc/passwd
grid:x:54331:54321::/home/grid:/bin/bash
File Permission