Commands:
In Splunk, to write a query we need to learn the various commands it offers. Each command comes with a special use case and can be used for its own purpose. Any search query that used transforming commands such as stats, chart etc. are known as Transforming search. Transforming commands uses the existing results and transform them into tables representing charts and stats visualizations.
Commands can broadly be categorized under categories as Transforming, Reporting, Filtering etc.
Some of the common commands are:
stats , top, rare, chart, timechart, dedup, rename, table, fields, eval, search, where
Concept of clause
These commands comes in very handy with transforming command. These are used to segregate data based on different entities.
Some of the frequent used clause are:
•as clause
•by clause
EVAL:
This is the widely used command in Splunk. It supports wide range of functions. It evaluated the particular expression and then it stores it in a new or existing fields.
1) . & + operator
2) Multiple chain
3) Comparison: if, case, coalesce
4) Conversion: tostring, tonumber
5) Date/Time functions: now(), strptime(), strftime()
6) Statistical functions: max(), median(), random()
7) Length functions: len(), substr()
Field Extraction Commands:
These are one of the most used feature of Splunk. This helps you to extract informative data from raw events as per business requirement. There are multiple ways to extract keywords like:
•Using Splunk UI through Splunk extract
•rex
•erex (using examples)
Joins
Join concept is used to combine the results of the sub search with that of master search. The only pre-requisite for this is that both the queries should have at least 1 field in common based on which both will be joined.
There are two types of joins that Splunk supports:
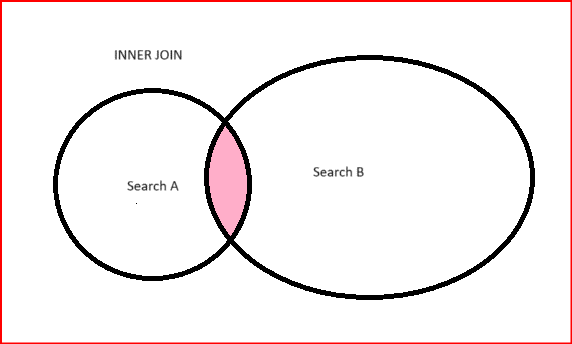
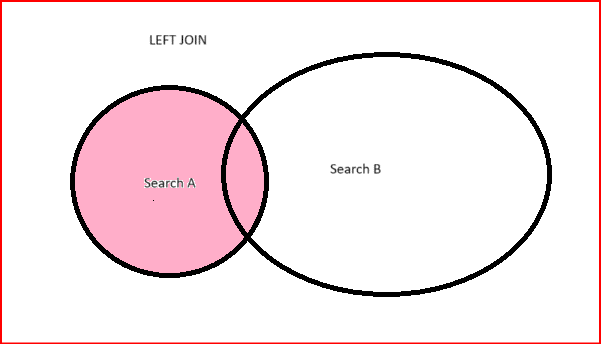
| INNER JOIN | LEFT/OUTER JOIN |
| It filters the events which are common in both search | It filters all the events from first search and then the common events from 2nd search |
Lookups
This command is used to enhance your extracted data with some related information from an external source file.
E.g.: You have the IP being tracked in the output of your query and then you have a static file which has a mapping of IP and its associated country. You can now map the static file to show case country information in the Splunk result.
Different types of command under lookup are:
* inputlookup
* lookup
* outputlookup
